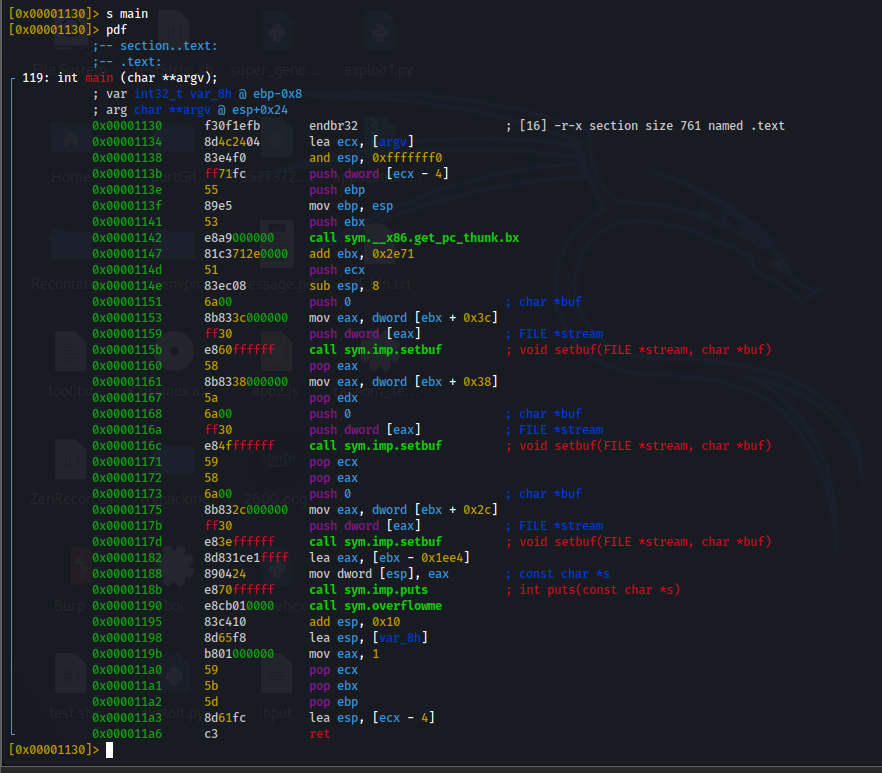
Binary Analysis Ctf . It is brought to you by the computer security lab at uc santa. Ctf writeup for last level 8. Web chapter 5 has the purpose of illustrating all these different tools of the trade which culminates with an intriguing. Web practical binary analysis book: Web practical binary analysis covers all major binary analysis topics in an accessible way, from binary formats, disassembly, and basic analysis to. Web binary exploitation is a broad topic within cyber security which really comes down to finding a vulnerability in the program and exploiting it. Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf challenges at the end of chapter 5. Web binary exploitation is the process of subverting a compiled application such that it violates some trust boundary in a way. The capture the flag challenge.
from medium.com
Web practical binary analysis book: Ctf writeup for last level 8. Web chapter 5 has the purpose of illustrating all these different tools of the trade which culminates with an intriguing. Web practical binary analysis covers all major binary analysis topics in an accessible way, from binary formats, disassembly, and basic analysis to. Web binary exploitation is a broad topic within cyber security which really comes down to finding a vulnerability in the program and exploiting it. Web binary exploitation is the process of subverting a compiled application such that it violates some trust boundary in a way. It is brought to you by the computer security lab at uc santa. Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf challenges at the end of chapter 5. The capture the flag challenge.
STDiO CTF I’m Binary Exploiter. หลังจากที่เราได้ไฟล์ binary… by
Binary Analysis Ctf Web chapter 5 has the purpose of illustrating all these different tools of the trade which culminates with an intriguing. The capture the flag challenge. Web binary exploitation is the process of subverting a compiled application such that it violates some trust boundary in a way. Web chapter 5 has the purpose of illustrating all these different tools of the trade which culminates with an intriguing. Web practical binary analysis covers all major binary analysis topics in an accessible way, from binary formats, disassembly, and basic analysis to. Ctf writeup for last level 8. It is brought to you by the computer security lab at uc santa. Web practical binary analysis book: Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf challenges at the end of chapter 5. Web binary exploitation is a broad topic within cyber security which really comes down to finding a vulnerability in the program and exploiting it.
From blog.kartone.ninja
An extensive step by step reverse engineering of a Linux CTF binary Binary Analysis Ctf Ctf writeup for last level 8. Web practical binary analysis book: Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf challenges at the end of chapter 5. Web practical binary analysis covers all major binary analysis topics in an accessible way, from binary formats, disassembly, and basic analysis to. It is brought to you by the. Binary Analysis Ctf.
From www.ctfiot.com
RUST BINARY ANALYSIS, FEATURE BY FEATURE CTF导航 Binary Analysis Ctf Web practical binary analysis book: Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf challenges at the end of chapter 5. Web chapter 5 has the purpose of illustrating all these different tools of the trade which culminates with an intriguing. Web binary exploitation is the process of subverting a compiled application such that it violates. Binary Analysis Ctf.
From github.com
GitHub retr0reg/Ret2GPT Ret2GPT Advanced AIpowered binary analysis Binary Analysis Ctf Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf challenges at the end of chapter 5. Web binary exploitation is the process of subverting a compiled application such that it violates some trust boundary in a way. Web binary exploitation is a broad topic within cyber security which really comes down to finding a vulnerability in. Binary Analysis Ctf.
From blog.kartone.ninja
An extensive step by step reverse engineering of a Linux CTF binary Binary Analysis Ctf Web binary exploitation is a broad topic within cyber security which really comes down to finding a vulnerability in the program and exploiting it. Web practical binary analysis book: Web practical binary analysis covers all major binary analysis topics in an accessible way, from binary formats, disassembly, and basic analysis to. Web chapter 5 of practical binary analysis by dennis. Binary Analysis Ctf.
From www.slideserve.com
PPT MachineLearning Assisted Binary Code Analysis PowerPoint Binary Analysis Ctf Web chapter 5 has the purpose of illustrating all these different tools of the trade which culminates with an intriguing. Web practical binary analysis book: Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf challenges at the end of chapter 5. Web binary exploitation is the process of subverting a compiled application such that it violates. Binary Analysis Ctf.
From practicalbinaryanalysis.com
Practical Binary Analysis Binary Analysis Ctf Web binary exploitation is the process of subverting a compiled application such that it violates some trust boundary in a way. Web chapter 5 has the purpose of illustrating all these different tools of the trade which culminates with an intriguing. Ctf writeup for last level 8. Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf. Binary Analysis Ctf.
From medium.com
STDiO CTF I’m Binary Exploiter. หลังจากที่เราได้ไฟล์ binary… by Binary Analysis Ctf Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf challenges at the end of chapter 5. It is brought to you by the computer security lab at uc santa. Web chapter 5 has the purpose of illustrating all these different tools of the trade which culminates with an intriguing. Web practical binary analysis book: Web binary. Binary Analysis Ctf.
From www.youtube.com
Automated Binary Analysis with Angr Sample Lesson Introduction YouTube Binary Analysis Ctf The capture the flag challenge. Ctf writeup for last level 8. Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf challenges at the end of chapter 5. It is brought to you by the computer security lab at uc santa. Web practical binary analysis book: Web binary exploitation is a broad topic within cyber security which. Binary Analysis Ctf.
From securityonline.info
angr A powerful and userfriendly binary analysis platform! Binary Analysis Ctf Web practical binary analysis covers all major binary analysis topics in an accessible way, from binary formats, disassembly, and basic analysis to. It is brought to you by the computer security lab at uc santa. Web practical binary analysis book: The capture the flag challenge. Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf challenges at. Binary Analysis Ctf.
From tuoyl.github.io
Binary System Analysis — TATpulsar 0.4.5 documentation Binary Analysis Ctf Web practical binary analysis book: Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf challenges at the end of chapter 5. Web chapter 5 has the purpose of illustrating all these different tools of the trade which culminates with an intriguing. It is brought to you by the computer security lab at uc santa. Web binary. Binary Analysis Ctf.
From hexterisk.github.io
Disassembly and Binary Analysis Fundamentals Pwn the world. — A noob's Binary Analysis Ctf Web chapter 5 has the purpose of illustrating all these different tools of the trade which culminates with an intriguing. Web binary exploitation is the process of subverting a compiled application such that it violates some trust boundary in a way. Ctf writeup for last level 8. Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf. Binary Analysis Ctf.
From www.semanticscholar.org
Figure 1 from A Method To Do Binary Analysis And Provide Smart Advisory Binary Analysis Ctf Web chapter 5 has the purpose of illustrating all these different tools of the trade which culminates with an intriguing. The capture the flag challenge. Web binary exploitation is the process of subverting a compiled application such that it violates some trust boundary in a way. Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf challenges. Binary Analysis Ctf.
From fairycn.github.io
Reverse Engineering fairycn Binary Analysis Ctf Web chapter 5 has the purpose of illustrating all these different tools of the trade which culminates with an intriguing. Web practical binary analysis covers all major binary analysis topics in an accessible way, from binary formats, disassembly, and basic analysis to. Web binary exploitation is a broad topic within cyber security which really comes down to finding a vulnerability. Binary Analysis Ctf.
From virgool.io
Binary Analysis PART One کد لاورز Binary Analysis Ctf Web practical binary analysis book: Web chapter 5 has the purpose of illustrating all these different tools of the trade which culminates with an intriguing. Web practical binary analysis covers all major binary analysis topics in an accessible way, from binary formats, disassembly, and basic analysis to. Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf. Binary Analysis Ctf.
From www.appknox.com
Comparison Between Binary Code Analysis & Source Code Analysis Binary Analysis Ctf Web practical binary analysis book: Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf challenges at the end of chapter 5. The capture the flag challenge. Web binary exploitation is a broad topic within cyber security which really comes down to finding a vulnerability in the program and exploiting it. Web practical binary analysis covers all. Binary Analysis Ctf.
From www.ctfiot.com
RUST BINARY ANALYSIS, FEATURE BY FEATURE CTF导航 Binary Analysis Ctf Web practical binary analysis book: It is brought to you by the computer security lab at uc santa. The capture the flag challenge. Web practical binary analysis covers all major binary analysis topics in an accessible way, from binary formats, disassembly, and basic analysis to. Web binary exploitation is a broad topic within cyber security which really comes down to. Binary Analysis Ctf.
From www.av-rd.com
Hex Editing for Archivists (Part 2) How to Read & Edit Binary Data Binary Analysis Ctf Ctf writeup for last level 8. It is brought to you by the computer security lab at uc santa. Web practical binary analysis covers all major binary analysis topics in an accessible way, from binary formats, disassembly, and basic analysis to. Web binary exploitation is a broad topic within cyber security which really comes down to finding a vulnerability in. Binary Analysis Ctf.
From tuoyl.github.io
Binary System Analysis — TATpulsar 0.4.5 documentation Binary Analysis Ctf The capture the flag challenge. Web chapter 5 has the purpose of illustrating all these different tools of the trade which culminates with an intriguing. Web chapter 5 of practical binary analysis by dennis andriesse contains several ctf challenges at the end of chapter 5. Web binary exploitation is the process of subverting a compiled application such that it violates. Binary Analysis Ctf.